What is Packet Sniffing ?
--> Packet sniffing is the practice of gathering, collecting, and logging some or all packets that pass through a computer network, regardless of how the packet is addressed. In this way, every packet, or a defined subset of packets, may be gathered for further analysis. You as a network administrators can use the collected data for a wide variety of purposes like monitoring bandwidth and traffic.
How This Works?
--> A packet sniffer, sometimes called a packet analyzer, is composed of two main parts. First, a network adapter that connects the sniffer to the existing network. Second, software that provides a way to log, see, or analyze the data collected by the device.
Requirements :-
1. Kali Linux OS
2. Ettercap(Pre-installed on Kali)
3.Wireshark(Pre-installed on Kali)
-----------------------------------------------Lets Start--------------------------------------------
Step 1:- First Of all connect Kali Linux to the network in which victim was connected.(Victims WIFI network)
Step 2:- Start Ettercap(GUI version) on Kali.
Step 3:- Turn on Sniffing at startup option, And select your interface from below option.(As per your connection type interface may vary).Then Click accept.
Step 4:- wait until the message started unified sniffing message shown below.
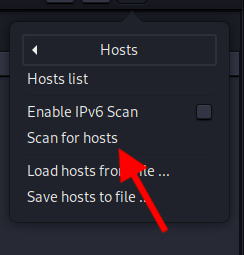
Step 5:- Make sure your Victim is in the network, to do that we had to scan the whole network.(Follow the below screenshots)Step 6:- Now the all the devices Connected to your network will be displayed.
Step 7:- To identify Your victim you can perform OS detection Scan through nmap on the following ip's.
Step 8:- I performed the map scans and I come to know That my Victim ip is 192.168.0.102 and the router ip was 192,168.0.1 . Now I will add my victim to the Target 1 and router to the target to to perform ARP poisoning attack.
Step 10:- After pressing OK the attack was started and Now you can monitor all the packets between your victim and router.(you can see the process in the below output box on the page of Ettercap).
Step 11:- To watch the Packets you need to open Wireshark on Kali.
Step 12:- After Opening Wireshark click your network interface.
Step 13:- You can see there are many packets shown here. We want packets of our victim only so we need to filter the list.to filter paste this on your Wireshark(use your victim ip instead of this)ip.addr == 192.168.0.102
Step 7:- To identify Your victim you can perform OS detection Scan through nmap on the following ip's.
Step 10:- After pressing OK the attack was started and Now you can monitor all the packets between your victim and router.(you can see the process in the below output box on the page of Ettercap).
Step 15:- Packet display that Victim is requesting for Facebook.com












Comments
Post a Comment
We respect your valuable Feedback